Securing Smart Homes: Mitigating Risks in the Connected World
Introduction
Smart homes are transforming the way we live, offering unprecedented convenience and efficiency. From voice-activated smart speakers to intelligent thermostats and security cameras, the Internet of Things (IoT) has created an ecosystem of connected devices. However, as our homes become smarter, they also become more vulnerable to cyber threats. This blog explores the risks posed by smart home technology and provides actionable strategies to mitigate them, highlighting lessons from the City of Aurora’s cybersecurity journey.
Understanding Smart Home Risks
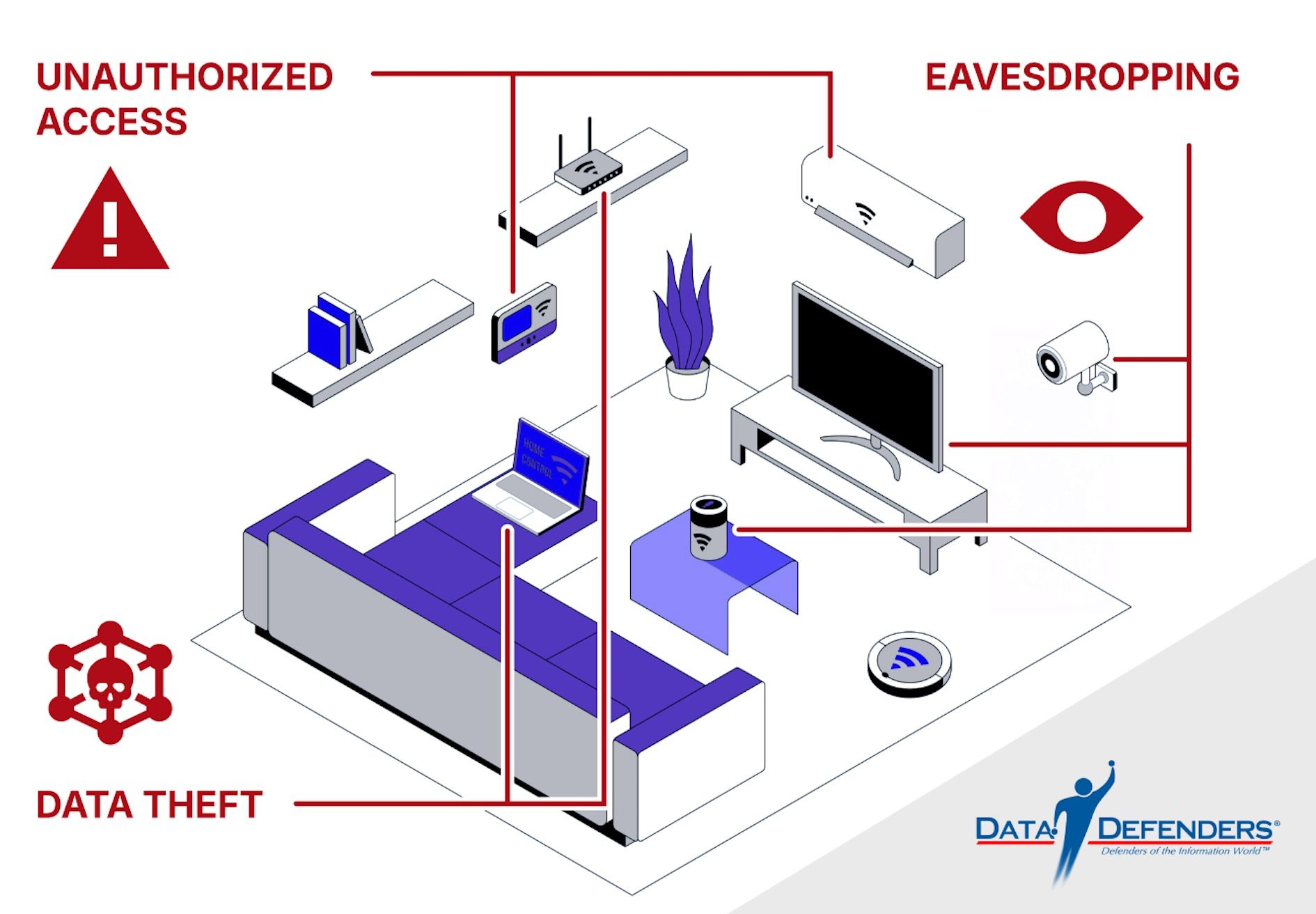
Smart home devices are designed to enhance daily living but often lack robust security measures, making them prime targets for attackers. Common risks include:
Unauthorized Access: Hackers exploit weak credentials to take control of devices
Eavesdropping: Smart speakers and cameras can be used for surveillance
Data Theft: Sensitive information stored on devices or transmitted over networks is a valuable target
Cybercriminals leverage these vulnerabilities to disrupt households and gain access to broader networks.
Vulnerable Entry Points in Smart Homes

1. Weak Passwords: Many devices come with default passwords that are easy to crack
2. Outdated Firmware: Regular updates are critical to patch security vulnerabilities
3. Unsecured Networks: Poorly configured Wi-Fi networks serve as gateways for cyberattacks
These weaknesses echo the broader cybersecurity challenges faced by municipalities, as highlighted in the Aurora Case Study.
Mitigation Practices

To safeguard your smart home ecosystem:
1. Secure Your Wi-Fi:
Use strong encryption (e.g., WPA3) and set a unique, complex password
Disable unnecessary features like guest networks or remote access
2. Update Firmware Regularly:
Enable automatic updates where possible
Periodically check for and apply patches for all connected devices
3. Choose Reputable Devices:
Purchase from manufacturers with a track record of security
Avoid off-brand devices that may lack robust support or updates
IoT-Specific Threats
The IoT ecosystem introduces unique threats, including:
- Device Spoofing: Attackers mimic legitimate devices to infiltrate networks
- Denial of Service (DoS): Flooding devices with traffic to disrupt operations
- Cross-Device Vulnerabilities: A compromised device can serve as a launching pad for attacks on other devices
Such risks necessitate adopting a layered security approach similar to those implemented in Aurora, where advanced tools like DataShield Cybersecurity 360°® reduced vulnerabilities.
The Role of Consumers

Consumers play a crucial role in securing their smart home environments:
- Education: Understand the risks and take proactive steps to secure devices
- Device Management: Regularly audit connected devices, removing those no longer in use
- Incident Response: Develop a plan for responding to potential breaches, such as disconnecting compromised devices
Aurora’s proactive stance on cybersecurity serves as a reminder that education and preparation are essential to building resilience.
Conclusion
The growing adoption of smart home technology comes with increased cybersecurity challenges. However, by understanding risks, addressing vulnerable entry points, and adopting mitigation practices, consumers can enjoy the benefits of a connected home without compromising security.

