Emerging Cybersecurity Threats for Enterprises: Staying Ahead of the Game
Introduction
As technology evolves, so do the tactics of cybercriminals. Enterprises face an increasing number of sophisticated threats, from AI-powered attacks to supply chain vulnerabilities, creating an urgent need to stay one step ahead. These threats jeopardize not just data but also critical infrastructure, operations, and trust.
In this blog, we explore five key emerging cybersecurity threats and offer actionable strategies to address them. Drawing insights from past challenges faced by municipalities and businesses, including the Aurora Case Study, we emphasize the importance of proactive measures in building resilient cybersecurity defenses.
AI-Powered Threats

Artificial Intelligence (AI) has become a double-edged sword in cybersecurity. While it bolsters defenses, it also empowers attackers to craft more sophisticated strategies. Common AI-driven threats include:
Deepfakes: Used for disinformation campaigns or social engineering attacks.
Automated Phishing: AI-generated phishing emails mimic real correspondence, tricking even the most vigilant recipients.
Adaptive Malware: Malware that evolves in response to detection mechanisms, making traditional defenses ineffective.
Organizations must deploy AI-driven defense tools, such as behavior-based threat detection systems, to counteract these intelligent attacks. As explored in The Rising Threat of Ransomware Attacks, AI is also enabling cybercriminals to create more targeted and devastating ransomware.
The Rise of IoT Risks
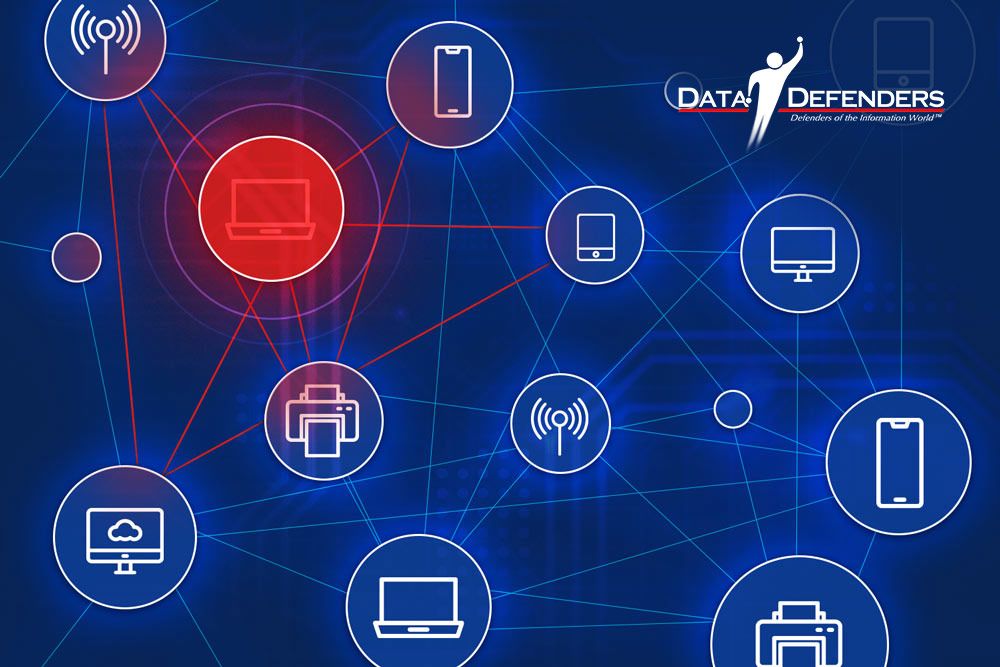
The Internet of Things (IoT) is transforming enterprise operations, but it comes with vulnerabilities. Connected devices often lack robust security measures, exposing enterprises to potential breaches. For example:
- Unsecured IoT devices can serve as entry points for network attacks.
- IoT systems in critical sectors, like healthcare or manufacturing, could be weaponized, leading to operational disruptions.
Mitigating these risks requires a layered security approach, including strict device authentication, network segmentation, and continuous monitoring. Similar to the public sector challenges discussed in Cybersecurity Challenges in the Public Sector, securing interconnected systems is vital for minimizing risk.
Supply Chain Security
Enterprises often overlook supply chain vulnerabilities, making them prime targets for cybercriminals. A compromised third-party vendor can provide an attacker access to an entire network. To reduce risks:
- Conduct thorough vendor risk assessments
- Enforce strict cybersecurity protocols for all suppliers
- Implement tools to monitor vendor activity and detect unusual behavior
The lessons learned in protecting municipal data, as detailed in Protecting Personal Data: Essential Cybersecurity Practices, emphasize the importance of ensuring partners adhere to the same high cybersecurity standards.
Zero Trust Frameworks

The Zero Trust model shifts the cybersecurity paradigm by assuming no user or system is inherently trustworthy. This approach minimizes the risk of insider threats and external breaches by requiring:
- Verification of every access attempt
- Limiting access to only what is necessary for the task
- Continuous monitoring and validation of activity
For enterprises navigating increasingly complex digital environments, Zero Trust frameworks are vital for safeguarding sensitive data and systems.
Future-Proofing Strategies
Cybersecurity is an ongoing battle that requires constant vigilance. Enterprises can future-proof their defenses through:
1. Continuous Threat Monitoring: Leverage AI and machine learning to identify and respond to threats in real-time.
2. Cybersecurity Awareness Training: Equip employees to recognize phishing attempts, weak passwords, and other risks.
3. Adaptive Defense Measures: Regularly update security protocols and systems to counteract emerging threats.
The Aurora Case Study exemplifies the power of combining robust tools, skilled professionals, and continuous monitoring to build a resilient cybersecurity framework.
Overcoming Challenges with MCOP
As enterprises combat evolving cybersecurity threats, partnering with a Managed Cybersecurity Operations Provider (MCOP) like Data Defenders is crucial. MCOP offers more than just security tools—it delivers a strategic framework that shifts cybersecurity from reactive to proactive, ensuring enterprises stay ahead of threats.
Secure Your Enterprise with MCOP
Cybercriminals are advancing their tactics—don’t wait to fall victim. Engage with our MCOP experts at Data Defenders to access cutting-edge cybersecurity solutions tailored to your enterprise. Protect your network, secure sensitive data, and maintain operational resilience.
Conclusion
Enterprises cannot afford to take cybersecurity lightly. With threats becoming increasingly sophisticated, staying ahead requires adopting advanced technologies, fostering a culture of security awareness, and collaborating with trusted experts.
Ready to bolster your defenses against emerging threats? Contact our team for expert guidance on implementing advanced cybersecurity solutions, including Zero Trust frameworks and AI-powered defenses.
For a deeper dive into real-world strategies, explore the Aurora Case Study and learn how Data Defenders helped municipalities stay ahead of cyber threats.