Artificial Intelligence and Cybersecurity: A Powerful Alliance
Introduction
Artificial intelligence (AI) is transforming industries, and cybersecurity is no exception. From identifying threats in real time to predicting and preventing future attacks, AI has become a crucial tool in defending against increasingly sophisticated cybercriminals. However, just as AI strengthens defenses, it also empowers attackers, raising new ethical and operational concerns.
In this blog, we’ll explore how AI is revolutionizing cybersecurity, its role in both defending against and enabling cybercrime, and what the future holds for this powerful alliance. Drawing on lessons from the Aurora Case Study, we’ll showcase how proactive strategies can leverage AI to safeguard critical infrastructure and sensitive data.
How AI is Revolutionizing Cybersecurity
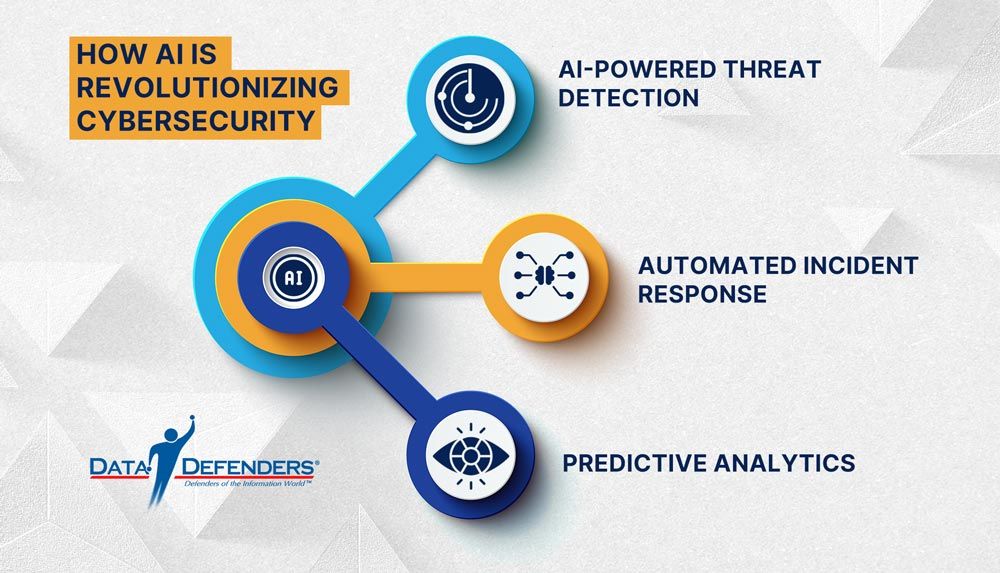
AI is reshaping cybersecurity by enabling faster, smarter, and more adaptive defenses. Key advancements include:
1. AI-Powered Threat Detection: AI systems analyze vast amounts of data to identify patterns that indicate potential threats. Unlike traditional systems, which rely on predefined rules, AI continuously learns and evolves, identifying even unknown threats.
2. Automated Incident Response: Automation reduces response times by taking immediate action when threats are detected, such as isolating compromised systems. This minimizes damage and prevents escalation.
3. Predictive Analytics: By analyzing historical data, AI predicts potential attack vectors, allowing organizations to bolster defenses proactively.
As highlighted in Week 7: Cloud Security for Small Businesses, AI-powered analytics also enhance cloud security by identifying vulnerabilities before they are exploited.
AI in Cybercrime

While AI enhances defenses, it also equips attackers with powerful tools to launch sophisticated attacks:
1. Phishing Campaigns: AI generates highly personalized phishing emails, making them more convincing and harder to detect.
2. Adaptive Malware: AI-powered malware evolves in real time to bypass traditional defenses.
3. Deepfakes: Cybercriminals use AI to create fake audio or video content for social engineering attacks.
In Week 1: The Rising Threat of Ransomware Attacks, we examined how ransomware attacks are evolving with the help of AI, becoming more targeted and devastating.
Real-Time Threat Mitigation

AI excels at identifying anomalies and mitigating threats before they escalate:
Behavioral Analysis: AI monitors user behavior to detect suspicious activity, such as unusual login locations or unauthorized data transfers.
Anomaly Detection: By analyzing network traffic, AI identifies and isolates threats, often in real time.
Incident Triage: AI helps prioritize threats based on severity, enabling faster and more efficient responses.
MCOPs utilize AI-driven behavioral analytics to detect anomalies across networks.
Through AI-enhanced automation, MCOPs ensure that suspicious activities are flagged and responded to in real time.
Incident triage and priority scoring, powered by AI, enable security teams to focus on the most critical threats.
With an MCOP like Data Defenders, organizations can ensure real-time threat mitigation with 24/7 monitoring, automated defenses, and AI-powered analytics.
As demonstrated in the Aurora Case Study, leveraging tools like DataShield Cybersecurity 360°® ensures real-time visibility and rapid response, critical for protecting municipal infrastructure.
Ethical Concerns
The rise of AI in cybersecurity also brings ethical challenges:
1. Privacy: AI systems often require access to sensitive data, raising concerns about surveillance and data misuse.
2. Bias in AI Algorithms: Flawed algorithms can lead to false positives or overlooked threats, disproportionately impacting certain users or systems.
3. Weaponization of AI: As AI becomes more advanced, the risk of its misuse by cybercriminals and state actors increases.
Balancing these concerns requires transparency, ethical AI design, and strict regulatory frameworks.
How MCOPs Leverage AI is Revolutionizing Cybersecurity
AI is reshaping cybersecurity by enabling faster, smarter, and more adaptive defenses. However, implementing AI-driven security requires expert oversight and strategic execution. A Managed Cybersecurity Operations Provider (MCOP) like Data Defenders can help organizations harness AI-driven defense solutions effectively.
By partnering with an MCOP, businesses and municipalities can:
- Leverage AI-powered threat detection to analyze vast datasets in real time.
- Implement automated security protocols that neutralize threats before they escalate.
- Shift from reactive security measures to a proactive cybersecurity stance.
MCOPs integrate AI-driven security analytics into existing infrastructures, ensuring comprehensive protection against emerging cyber threats.
Future of AI in Cybersecurity
AI will continue to evolve, and organizations must adapt their security models to keep pace with sophisticated threats. MCOPs are at the forefront of this transformation, offering solutions that integrate:
Adaptive AI Security Systems that learn from past attacks and adjust defenses dynamically.
Federated AI Learning to enhance cybersecurity intelligence across multiple organizations.
AI-Augmented Cybersecurity Teams where human analysts collaborate with AI to detect, analyze, and respond to cyber threats with unmatched precision.
Organizations that partner with an MCOP gain access to cutting-edge AI-powered security solutions, ensuring they stay ahead in the cybersecurity arms race. In Week 4: Emerging Cybersecurity Threats, we explored how advancements like these are shaping the future of enterprise security.
Empower Your AI-Driven Cybersecurity Strategy with MCOP

AI-driven cybersecurity demands constant vigilance and expert management. A Managed Cybersecurity Operations Provider (MCOP) like Data Defenders delivers AI-powered security solutions, ensuring your organization remains protected against evolving cyber threats.
For practical insights into how AI can transform cybersecurity, check out Cybersecurity Best Practices for Municipalities, which highlights the importance of proactive strategies.
Ready to explore the transformative potential of AI in cybersecurity? Contact our experts to learn how solutions like DataShield Cybersecurity 360°® can bolster your defenses. For real-world inspiration, explore the Aurora Case Study to see AI in action.

